
新办了一张信用卡,注册了Amazon的AWS,在上面试着搭建了Virtual Private Network.
具体步骤如下:
sudo -sapt-get install pptpdvi /etc/pptpd.conflocalip 192.168.9.1remoteip 192.168.9.11-30vi /etc/ppp/optionsms-dns 8.8.8.8ms-dns 8.8.4.4vi /etc/ppp/chap-secretspptpd *//设置用户名和密码vi /etc/sysctl.confnet.ipv4.ip_forward = 1sysctl -pvi /etc/rc.local iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADEservice pptpd startchkconfig pptpd on
在AWS的站点上设置安全组的对应的端口值即可。如下图所示:



注意Virtual Private Network对于各种流量走的都是这台云服务器,所以还是悠着点哦,信用卡透支太多还是不必要的。
备注:ssh连接服务器后的命令汇总:
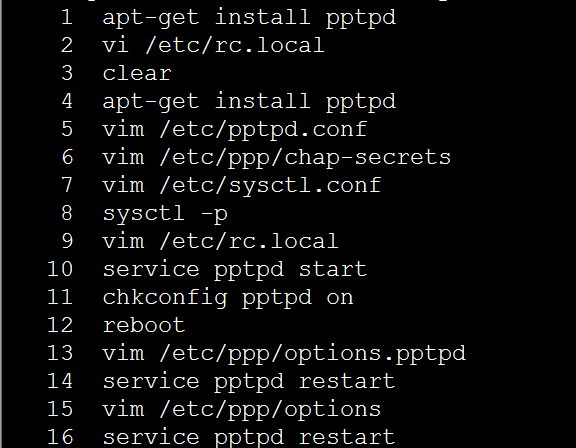
备注知识点:
关于什么是
pptp
The Point-to-Point Tunneling Protocol (PPTP) is a method for implementing virtual private networks. PPTP uses a control channel over TCP and a GRE tunnel operating to encapsulate PPP packets.
The PPTP specification does not describe encryption or authentication features and relies on the Point-to-Point Protocol being tunneled to implement security functionality. However, the most common PPTP implementation shipping with the Microsoft Windows product families implements various levels of authentication and encryption natively as standard features of the Windows PPTP stack. The intended use of this protocol is to provide security levels and remote access levels comparable with typical VPN products.
A specification for PPTP was published in July 1999 as RFC 2637 and was developed by a vendor consortium formed by Microsoft, Ascend Communications (today part of Alcatel-Lucent), 3Com, and others. PPTP has not been proposed nor ratified as a standard by the Internet Engineering Task Force.
关于什么是
Virtual Private Network
A Virtual Private Network (VPN) is a network technology that creates a secure network connection over a public network such as the Internet or a private network owned by a service provider. Large corporations, educational institutions, and government agencies use VPN technology to enable remote users to securely connect to a private network.
A VPN can connect multiple sites over a large distance just like a Wide Area Network (WAN). VPNs are often used to extend intranets worldwide to disseminate information and news to a wide user base. Educational institutions use VPNs to connect campuses that can be distributed across the country or around the world.
In order to gain access to the private network, a user must be authenticated using a unique identification and a password. An authentication token is often used to gain access to a private network through a personal identification number (PIN) that a user must enter. The PIN is a unique authentication code that changes according to a specific frequency, usually every 30 seconds or so.
Protocols
There are a number of VPN protocols in use that secure the transport of data traffic over a public network infrastructure. Each protocol varies slightly in the way that data is kept secure.
IP security (IPSec) is used to secure communications over the Internet. IPSec traffic can use either transport mode or tunneling to encrypt data traffic in a VPN. The difference between the two modes is that transport mode encrypts only the message within the data packet (also known as the payload) while tunneling encrypts the entire data packet. IPSec is often referred to as a "security overlay" because of its use as a security layer for other protocols.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) use cryptography to secure communications over the Internet. Both protocols use a "handshake" method of authentication that involves a negotiation of network parameters between the client and server machines. To successfully initiate a connection, an authentication process involving certificates is used. Certificates are cryptographic keys that are stored on both the server and client.
Point-To-Point Tunneling Protocol (PPTP) is another tunneling protocol used to connect a remote client to a private server over the Internet. PPTP is one of the most widely used VPN protocols because of it's straightforward configuration and maintenance and also because it is included with the Windows operating system.
Layer 2 Tunneling Protocol (L2TP) is a protocol used to tunnel data communications traffic between two sites over the Internet. L2TP is often used in tandem with IPSec (which acts as a security layer) to secure the transfer of L2TP data packets over the Internet. Unlike PPTP, a VPN implementation using L2TP/IPSec requires a shared key or the use of certificates.
VPN technology employs sophisticated encryption to ensure security and prevent any unintentional interception of data between private sites. All traffic over a VPN is encrypted using algorithms to secure data integrity and privacy. VPN architecture is governed by a strict set of rules and standards to ensure a private communication channel between sites. Corporate network administrators are responsible for deciding the scope of a VPN, implementing and deploying a VPN, and ongoing monitoring of network traffic across the network firewall. A VPN requires administrators to be continually be aware of the overall architecture and scope of the VPN to ensure communications are kept private.
Advantages & Disadvantages
A VPN is a inexpensive effective way of building a private network. The use of the Internet as the main communications channel between sites is a cost effective alternative to expensive leased private lines. The costs to a corporation include the network authentication hardware and software used to authenticate users and any additional mechanisms such as authentication tokens or other secure devices. The relative ease, speed, and flexibility of VPN provisioning in comparison to leased lines makes VPNs an ideal choice for corporations who require flexibility. For example, a company can adjust the number of sites in the VPN according to changing requirements.
There are several potential disadvantages with VPN use. The lack of Quality of Service (QoS) management over the Internet can cause packet loss and other performance issues. Adverse network conditions that occur outside of the private network is beyond the control of the VPN administrator. For this reason, many large corporations pay for the use of trusted VPNs that use a private network to guarantee QoS. Vendor interoperability is another potential disadvantage as VPN technologies from one vendor may not be compatible with VPN technologies from another vendor. Neither of these disadvantages have prevented the widespread acceptance and deployment of VPN technology.
扯了这么多,说点儿基本的,下面是从网络上摘取的关于网络协议的解释:
What is a Network Protocol?
Networks are how computers communicate with each other. A protocol is a particular standard, or language, that the computers use to understand each other. Think of the network as a road, and the protocol as the rules set down for using that road.
Various Network Protocols
There are many different network protocols. Some dictate how computers communicate over a local network - that is, computers in a local area that directly communicate over a network router. Other protocols govern how computers communicate over a remote network - generally speaking, via the internet. One of the most notable protocols is Internet Protocol, or IP. It is the main network protocol governing the internet.
The most commonly used version is Internet Protocol version 4, or IPv4, though systems are slowly transitioning to version 6. Computers are identified within Internet Protocol using an unique numerical identifier called an IP address. These are often set up by specialists known as network administrators.
TCP and Network Protocols
While Internet Protocol is a single network protocol, it is also part of a larger family called Internet Protocols. TCP, or Transmission Control Protocol, is used hand-in-hand with the IP protocol to create a standard known as TCP/IP.IP sends various pieces of information over a network. These pieces of data are known as packets. TCP combines those packets of IP data into an efficient and accurate request to another computer. It helps ensure that packets are not lost when transmitted over the network.
Thus, TCP/IP is the combined standard that computers use to communicate over the Internet.There are other forms of protocols that work within the IP family. HTTP, or Hypertext Transfer Protocol, allows a web browser to communicate with a web server. You may have seen HTTP included in many world wide web addresses.FTP, or File Transfer Protocol, is another common protocol, designed for efficient file transfer over the internet. Both HTTP and FTP deliver information in concert with the TCP/IP protocol.